Access Control Systems
Touchless, Cloud-Based Access Control
Hands-Free & Touchless
Wave to Unlock with the phone in your pocket
Or Mobile Unlock
Use your phone to unlock
Cloud-Based
Manage your access from anywhere
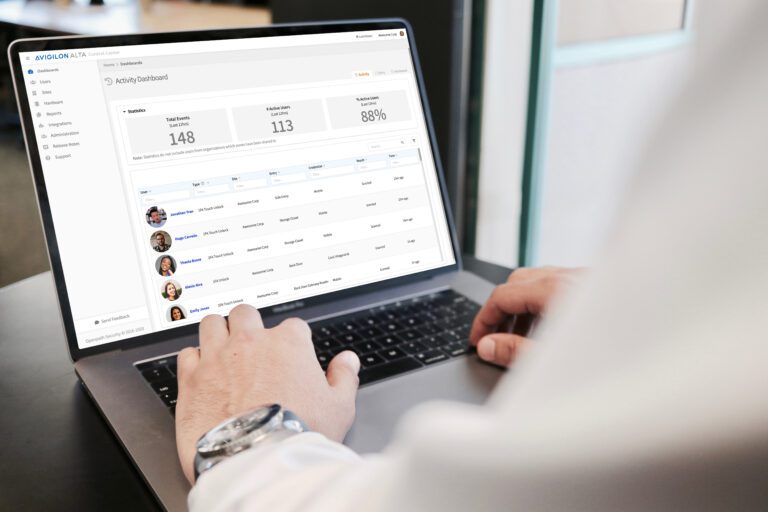
Real-Time Reporting – 24/7 access activity logs
Guest Pass – One-time access with easy SMS or email link
Triple Unlock Patented Technology

Convenient Keyless Access with Video
Our mission is to provide convenient building access control systems to secure any environment. As a certified CDVI and Avigilon Alta formerly known as Open Path, we design, install and help manage smart, customizable access control solutions.
- PROTECTION PLUS utilizes cutting-edge software and modern hardware for their custom, integrated security solutions and is a leading Toronto access control system installer. PROTECTION PLUS is a top provider for Toronto and the GTA, including Mississauga, Hamilton, and the Durham and York regions.
When installing your access control system, Toronto professionals recommend keyless door entry with built-in video capabilities for protecting and managing access to an area at any given time. In addition to regulating access to your building,
your access control system installer can also help you restrict entry to interior areas. Avigilon Alta cloud-based access control system is favoured for the intuitive software for easy management, simple hardware installation, and readers with built-in cameras to combine smart mobile entry with video security in a single device at the door. PROTECTION PLUS will design commercial building access control systems that address needs for your file rooms, server rooms, inventory storage areas, and other areas that require high-level physical security.
Applications of a Card Access Control System
Here are some of the most common applications for access control across industries:
-

With the evolution of more flexible working conditions, businesses must provide next-generation security featuring fast and reliable access control. A key card access control system is a reliable way to give employees more flexible access. Introducing touchless and mobile-based options for wireless door access control systems is also popular, as it minimizes management for on-site teams.
-

The right access control system can significantly impact your bottom line. Given high turnover rates in the retail industry, smart access control allows employers to add, remove and schedule access for staff as needed without extra labour. For managing multiple retail locations, a cloud-based access control system gives administrators remote access to all their security data and controls for greater flexibility.
-

With rising rent in metropolitan areas and a greater desire for better security, landlords are turning to smarter access control for their communities. Cloud-based and mobile access control systems let property managers easily accommodate visitors, deliveries, and maintenance without having to staff a reception or lobby desk with 24/7 security. State-of-the-art integrated systems are also equipped to connect with tenant apps for a better renter experience.
-

Whether you’re in a Primary school, Secondary school, or a university setting, protecting students and teachers is a top priority. As security incidents become more prevalent on campuses, school administrators must ensure that students feel safe in their learning environments. A key card access control system is a great way to allow authorized access to the campus for faculty and staff. PROTECTION PLUS can set you up with wireless door access control systems equipped with remote lockdown for better emergency response and improved school safety.

-

Religious institutions have recently become more vulnerable to vandalism, burglary and violence. At the same time, they wish to project a welcoming atmosphere and openness to all of their congregants and staff. A state-of-the-art key card access control system can solve this problem by blending into its physical surroundings, supporting multiple access methods to foster accessibility, and creating a system of record that logs access activity for easy auditability. Remote access is a key feature of cloud-based access control systems for houses of worship and enables remote system lockdown for improved safety and emergency response.
-

Access control systems in the healthcare industry require an innovative approach with easy ingress and egress for main entries but limiting access to narcotics, substances, laboratory equipment, and medical records. Additionally, any hospital access control system must be able to easily accommodate changing shifts and employee schedules and facilitate quick and easy access throughout the building. Wireless door access control systems are an excellent option for hospital security, as they provide detailed audits of entry activity. Paired with cloud-based access control system software, hospitals can easily adjust permissions and door schedules remotely for greater flexibility.
-

Due to strict access and data protection regulations, securing governmental facilities requires meeting several technical security standards. Key card access control systems managed on-premise can provide government buildings with better physical security, limiting who has the authorization to enter the building. Installing a wireless door access control is key for high-security areas, as it prevents unauthorized individuals from gaining entry and provides a clear report for better auditability.
-

As companies like Airbnb change the hospitality industry, hotels are under increased pressure to make their facilities amenable to guests while maintaining a high level of security. A mobile, cloud-based access control solution can help mitigate the challenges. Hotel guests can unlock their room doors with their phones, activating the wireless door access control system via a convenient app. This eliminates the older key card access control system models and makes it easier for guests to check in and access their rooms at any time. Wireless door lock systems are also famous for keeping hotel amenities safer, such as controlling access to fitness centres, pools, office centres, and conference spaces.
-

ULC, banking, and jewellery applications – High-risk businesses are vulnerable to various threats, including robbery, fraud and terrorism. However, brick-and-mortar properties are often limited on the on-site personnel they can employ for security. Installing a cloud-based access control system like Avigilon Alta allows them to efficiently manage the security at each facility without requiring the physical presence of an on-site administrator. Features like automated alerts help keep managers informed and empower proactive security management with remote access to reporting, permissions, and door locks.
-

Today’s warehouses are becoming smarter and more automated than ever. For facilities still using traditional locks or keypads to get into the room, a lost key can create a significant expense and critical codes are easily compromised. Through a smart cloud-based access control system, warehouses and storage facilities can ensure their inventory is always safe. The platform allows warehouse managers to issue credentials, change door schedules, and even remotely unlock the door without being on-site.
-

There are many moving parts for manufacturing facilities, so security is a top priority. A key card access control system can help provide a better picture of who is accessing specific spaces with improved auditability. From unlocking the door for a last-minute delivery to expediting insurance claims to ensuring loss prevention, a cloud-based access control system is a more innovative way to keep manufacturing facilities safe and secure.
Show how a cloud-based Protection Plus access control system can work for your business, with the fastest, most reliable mobile unlocking experience and a complete range of hardware and software designed to scale with ease.
RE/MAX Realtron Realty Testimonial
Top access control systems features
Access Control Systems
Access control in your facilities is a significant part of protecting your business. In addition to regulating access to your building, you may also need to restrict entry to some inside areas with higher security needs, such as file rooms, server rooms, inventory storage areas, etc. You could give employees different keys to different rooms and then need to change locks with employee turnover, but this is cumbersome, costly, and not very effective.
You can eliminate these hassles by having PROTECTION PLUS® install an electronic access control system, such as Avigilon Alta.
Our mission is to improve convenience and security in the access control environment. Avigilon Alta creates innovative, customizable entry control solutions. By combining sleek hardware with cloud-based enterprise software, Avigilon Alta enables mobile, hands-free entry and makes system management more accessible than ever.
The scalable, open platform seamlessly integrates with best-of-breed partners across a wide range of categories used to most efficiently run your business, including; Tailgating, Video Management & Surveillance, Lockdown, Active Directory Platforms, Visitor Management, Building Automation, and so many more.
PROTECTION PLUS® is proud to be one of first Avigilon Alta Canadian authorized dealer. Our trained and certified technicians and sales representatives will facilitate your access control systems’ implementation from the first step to the last.
PROTECTION PLUS stands behind the Avigilon Alta lifetime equipment warranty*.
* some conditions apply.
ASK US FOR A NO OBLIGATION DEMONSTRATION AND QUOTATION of the STATE-OF-THE-ART access control system
What type of access control is best in the era of Covid-19?
Access Control systems can unlock doors in a number of ways.
- Keyfob
- Phone app
- Smartphone that works as a fob
- By pushing the reader
- And with a wave
Not all systems can use all methods. Best to do your research before installation. The wave feature minimizes contact however, to take full advantage, this feature should be incorporated with a strike release so the door not only unlocks, but opens automatically as well.
Where can access control be used?
most common applications for access control include:
- Commercial offices
- Retail
- Multi-tenant housing
- Education
- Religious institutions
- Healthcare
- Government
- Hi-Risk; ULC, Banking, Jewellery, applications
- Warehousing and Shelf Storage
How many doors can be serviced by an access control system?
Small business is the heartbeat of the Ontario economy, and the vast majority of access control systems control 3 doors or less, but expansion capacity can exceed 100 doors.
What is access control?
Access control is an entry system that enables an institution or business to control access to the protected facility. Access can be limited, controlled and recorded at specific times to certain areas of a building.
Can an access control system be integrated with other security solutions?
Absolutely. At PROTECTION PLUS, we design access control to work seamlessly with wider security ecosystems. We connect card readers, keypads, or mobile credentials to intrusion alarms, CCTV, fire panels, visitor management software, and building automation. When a door is forced, integrated video bookmarks the event, and an alert appears on your monitoring dashboard in real time, ensuring no incident is overlooked. Unified data simplifies investigation; one report shows who entered, camera footage, and alarm status. Because we handle design, installation, and ongoing support, you enjoy a single, coherent platform instead of juggling multiple vendors for informed decisions daily.
Can existing doors and locks be upgraded to work with access control?
Yes. Upgrading existing doors and mechanical locks is often the most cost-effective way to introduce access control. We conduct a site survey first, measuring frame depth, door material, strike plate type, and power availability. When conditions allow, we retrofit electrified strikes or magnetic locks, install wireless readers, and keep your current hardware where possible to preserve aesthetics. Hinges, closers, and fire ratings remain compliant; only the credential method changes. Because we program everything in-house, migration is smooth: keys can still open during transition, then we phase in cards, fobs, or mobile credentials without disrupting operations for staff and visitors.
Is cloud-based access control available?
We offer cloud-based access control that eliminates on-site servers and gives you secure, anytime management from any device with a browser. Our encrypted platform resides in Canadian data centres meeting SOC 2 and PIPEDA requirements, so your credentials stay private and compliant. Through a single dashboard, you can add or revoke users, adjust schedules, and run activity reports without visiting the building. Automatic firmware updates, redundancy, and 24/7 monitoring reduce IT overhead. If preferred, we integrate video, alarms, and visitor management into the same cloud interface, giving you full situational awareness while lowering capital expenditure and simplifying future expansions.
Can an access control system be integrated with other security solutions?
Certainly, we architect access control to communicate with your current security technologies so every component reinforces the next. For example, we link badge events to CCTV presets, directing cameras automatically toward the accessed doorway, while intrusion panels arm or disarm based on credential privileges. Elevator controls restrict floor access, and building management systems adjust lighting or HVAC when occupancy changes. We even push event data to HR and time-clock software to streamline payroll and compliance audits. By letting disparate systems share real-time information, we create a more innovative, proactive environment that deters threats, speeds response, and improves operational efficiency for everyone.
Electronic Card Access Control Systems Toronto

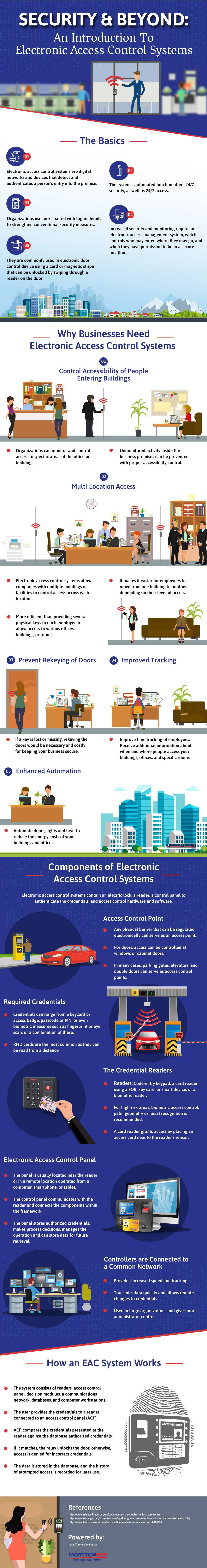
Keeping your organization safe is always top of mind. The more sensitive your operation, the more secure it must remain. Using electronic access control systems (EAC) provides the protection you need in the simplest and most accessible manner. They offer digital networks and devices designed to detect and authenticate entry onto your premise. These systems effectively operate 24/7 with customized access provided based on the person entering your facility. You can use the system paired with log-in details to enhance your security measures. You will have total control over who enters every area within your facility, and determine who is allowed access to each area. You can even limit access to certain areas based on the time and day of the week. With the onslaught of COVID-19, having touchless security and entry options are more important than ever. Combining hygienic entry options in hand with a security system that allows you to dictate permission-based entry creates a state-of-the-art security system ideal for any organization.
Combined Entry and Security
Your electronic access control system is highly customizable, allowing you to use them with other lock and security measures. Most commonly, they are partnered with electronic door control devices unlocked using an RFID card, PIN code or biometric scans. Today, touchless options are in high demand to prevent the spread of viruses like COVID-19.
The Benefits of Electronic Access Control Systems
There are many reasons you need an electronic access control system:
- Control: You have better control over who enters your organization and the areas they can access. You can monitor and control access depending on the clearance for each visitor or employee. You can also prevent unmonitored activity inside your premises based on accessibility control.
- Multi-location Access: COVID-19 has made it more difficult to ensure that essential employees access unique facilities. Using electronic access control systems, you can control multiple buildings from one system. Introducing touchless and wave to open options reduces touchpoints throughout your facility while making it easier for employees to move from location to location based on their approved access level.
- Avoid Rekeying of Doors: A lost or missing key is costly, as it requires rekeying the doors. Your EAC makes rekeying unnecessary.
- Improved Tracking: Your system allows you to see who is on your premises, where they are and when they enter and leave to look for potential security and performance issues.
Perhaps best of all, you can integrate your system with various business apps and devices. This allows you to use your access control system for functions such as visitor management, lighting and room booking.
Components of Electronic Access Control Systems
Your electronic access control systems consist of:
Access Control Point (Entries)
Manage and create regulated physical barriers for secure access points, including doors, parking gates, storage cabinets and elevator floors, where access is restricted.
Credentials
Credentials include:
- RFID key cards and fobs: These are the most hygienic form of access control. You can choose:
- Proximity cards to communicate using low-frequency fields and provide no encryption.
- Contactless smart cards communicate using high-frequency fields.
- Swipe cards are considered less secure than RFID cards because they’re usually not encrypted and are easy to clone.
- PIN code: PIN readers use PIN codes to grant access, but are not recommended for areas that require high security.
- Biometrics: This would include entry via fingerprints or palm veins, but present a greater possibility to malfunction in dusty or humid environments.
- Mobile: Employees use their smartphones to make unlock requests by touching the reader.
You can choose to use a single type of credential or a combination suited to your specific needs.
Credential Readers
Credential readers are installed near the entries to allow staff or visitors to use their credentials to send the inputs to the Access Control Unit (ACU) using a wired or wireless connection. High-risk areas are more secure using biometric access control, palm geometry or facial recognition.
Electronic Access Control Unit
The ACU is used to receive the credential data from the reader. Once the proper credential is used, access is provided, and the ACU will unlock the door. The ACU can make processing decisions and manage data such as credentials, PINS, and other security features.
Locking Hardware & Access Control Software
This is the functioning electromagnetic locks, push bars, and other electrified hardware used to configure entries. It is managed using access control software, allowing the information to be defined in the application syncs with the ACU to determine if access should be granted.
How an EAC System Works
While all these parts and functions might seem complicated, in its most basic form an EAC system is quite simple. It works in the following way:
Step 1 – Authentication: First, the user must present their credentials to the access points’ reader. The reader sends the data to the ACU, so it can determine if the credentials meet the access point’s requirements.
Step 2 – Authorization: Next, the ACU determines whether the system recognizes the user and if they have the right kind of credential to trigger entry. This process can include a vast series of data, including:
- If the user has access to the entry that they’re trying to unlock
- If they are using the predefined allowed credential types and trigger types
- If they are making the unlock request within any schedules defined on the entry
It will also ensure that the other restrictions, such as a system lockdown, are not currently triggered.
Step 3 – Access: Once authorization is complete, commands are sent from ACU to the door-locking hardware to unlock the entries.
Step 4 – Manage: Administrative software is used to sync automatically with internet-connected ACUs for adding or removing entries, user credentials, schedules, and alerts.
Step 5 – Audit: Your organization’s administrators can generate reports for access logs, including both user activity and entry activity, by auditing the access control system. This ensures there are no issues with accessing entries, and the system is working correctly.
Despite the many steps involved in entry and authentication, it all happens almost instantly, providing quick access for authorized employees or visitors. The EAC system is highly customizable, efficient, and hygienic, providing any organization large or small with a dependable access process.